



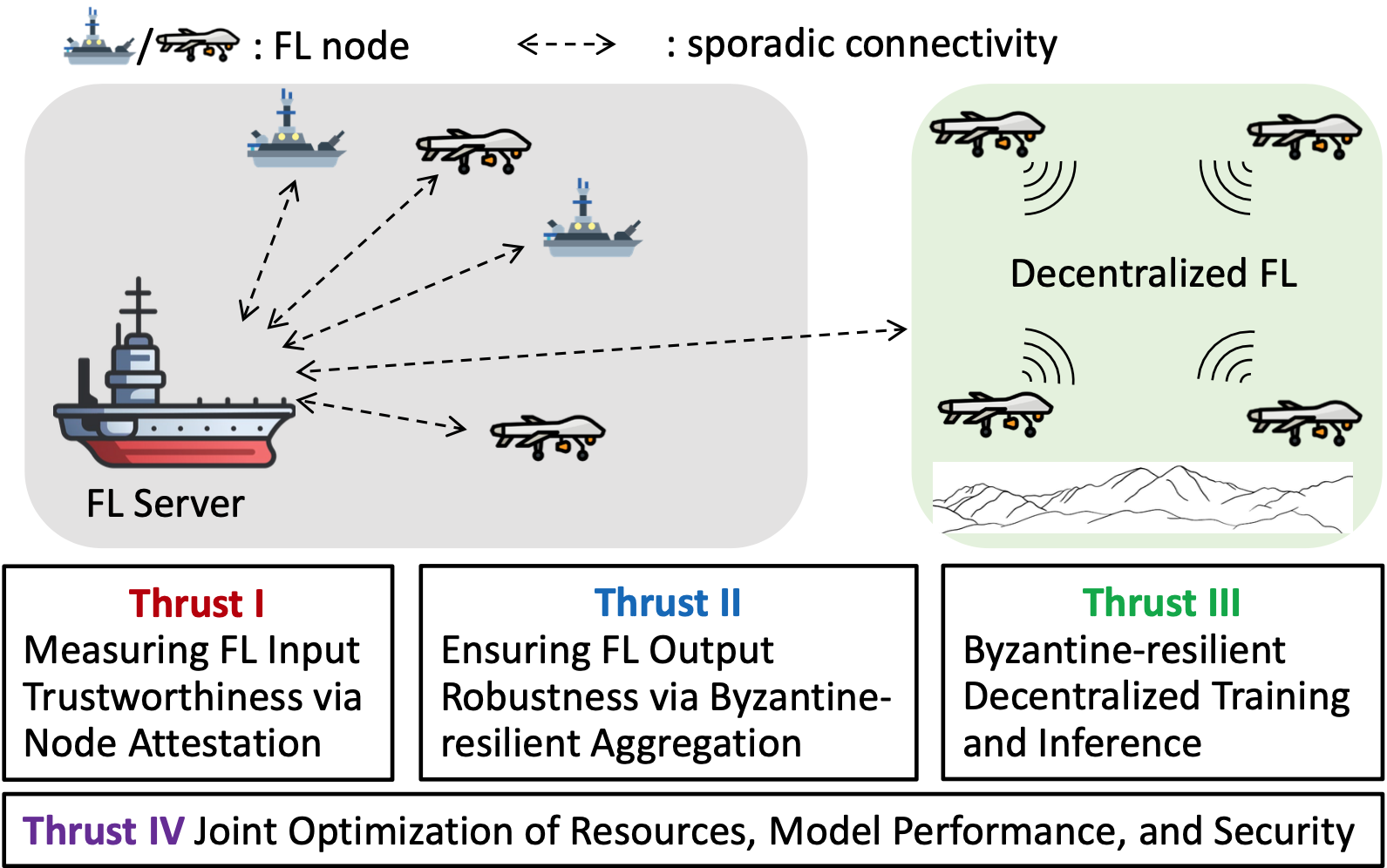
The objective of the project is to establish the theory and system foundation to address security challenges in federated learning in resource-constrained and sporadically connected military networks, particularly in hostile environments. The primary threat considered here is Byzantine attacks, where Byzantine nodes (i.e., compromised participants in an FL system) exhibit arbitrary and malicious behaviors. Such behaviors can include refusing to cooperate, sending incorrect information, or trying to deceive other participants in the system. To achieve their malicious goals, Byzantine nodes may send conflicting information to different recipients. Byzantine attacks can lead to significant consequences on FL systems. Byzantine nodes can inject malicious input into the learning process, leading to model poisoning and slower convergence or convergence to suboptimal models. The sporadic connectivity in the network makes the situation more challenging. In extreme cases, while losing connectivity to the FL server, Byzantine nodes can disrupt the consensus process, resulting in erroneous actions taken in critical decision-making. This project aims to mitigate such Byzantine attacks in mission-critical military FL systems by building Byzantine resiliency into FL systems, particularly for resource-constrained and sporadically connected networks.
Lead: Dr. Wenjing Lou
Research Goal: This thrust considers the sporadic connectivity between the FL server and FL nodes, some of which are Byzantine actors. We take a systems approach to derive a principled method to assess the trustworthiness of information from FL nodes. We will develop new remote attestation primitives that will allow contributing nodes to demonstrate cryptographically that their submitted information follows specific security policies. Specific to FL, attestation will include both data integrity and learning program integrity. Asynchronous attestation in sporadically connected networks with resource-constrained embedded devices is also a focus of this exploration.
Lead: Dr. Ning Wang
Thrust II then takes a data-centric approach, aiming to develop robust and efficient learning algorithms that keep adversarial influence to the minimum, ensuring robust FL output even in the face of Byzantine inputs. The attestation results from Thrust I, as a good assessment of the trustworthiness of the input data, can be integrated to enhance the learning accuracy and speed up the learning rate.
Lead: Dr. Yang Xiao
This thrust considers the most challenging scenario where a group of FL nodes has to work in a self-organized fashion to make critical learning or inference decisions collectively when losing connectivity to the FL server. We will develop new consensus-based Byzantine-resilient decentralized FL approach to enable trustworthy training and inference decision-making in this challenging scenario. The defense builds on the observation that nodes deployed in close proximity in the battlefield share similar worldviews to develop new consensus-based decision-making and adaption methods without the need for proof of work or proof of stake.
Leads: Dr. Tom Hou and Dr. Yi Shi
This thrust will thoroughly analyze the system resource requirements of various defense mechanisms, and their impacts on model performance. Both model-based optimization and learning-based optimization will be developed to allow optimal integration of the defenses to dynamically adapt to the changing network and computation capabilities of the system.